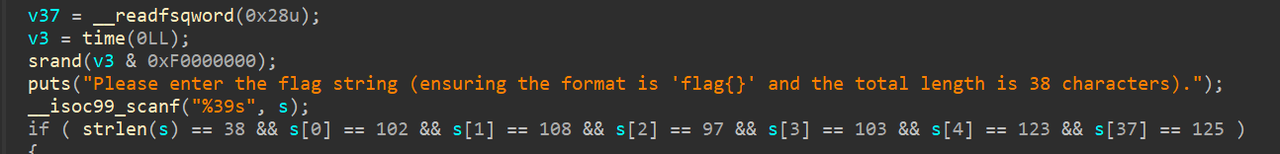
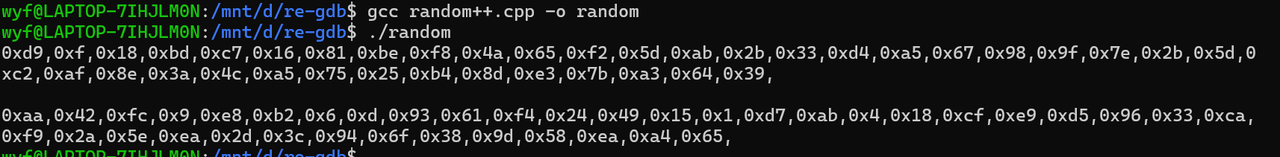
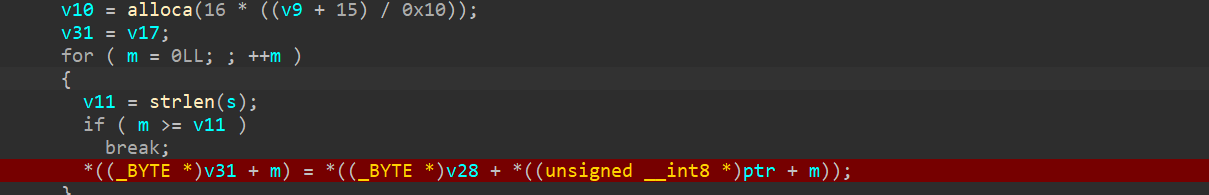
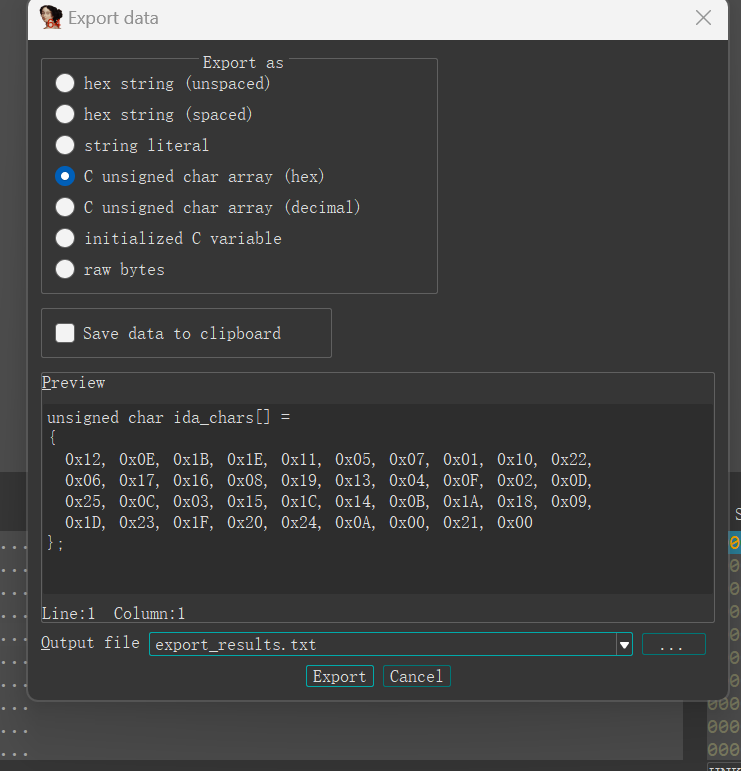
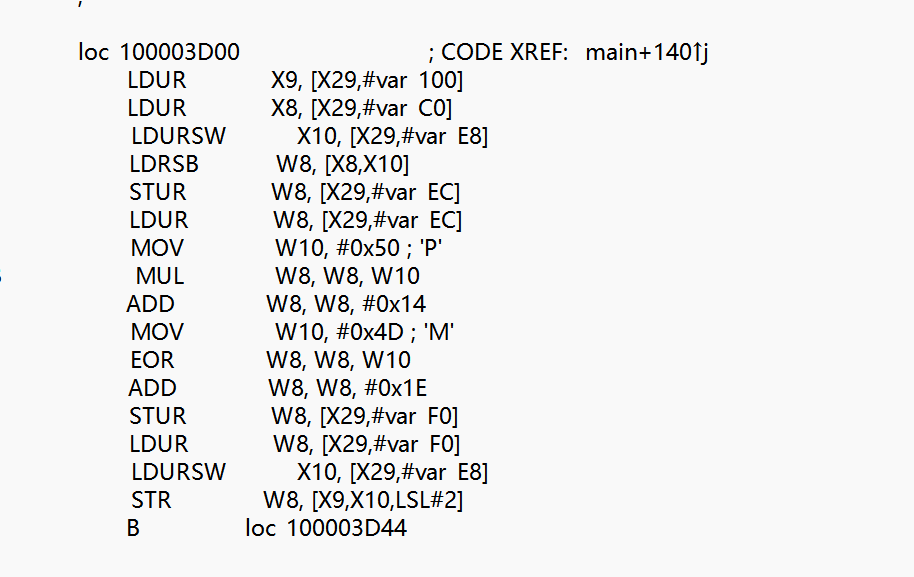
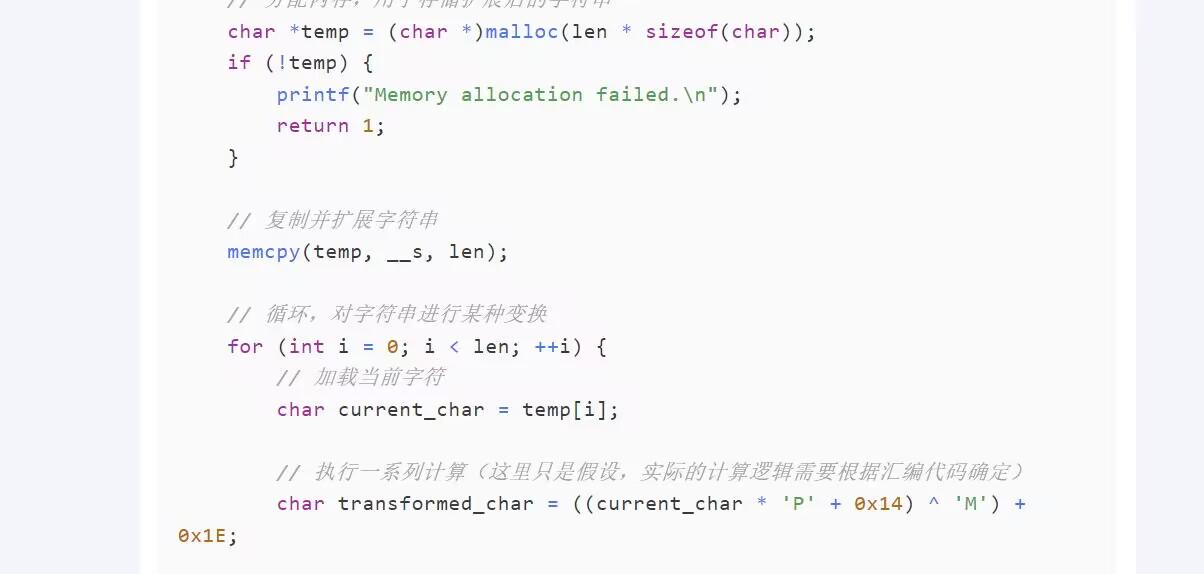
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
| #include<stdlib.h>
#include<stdio.h>
#include<memory.h>
#include<string.h>
int main()
{
const char* ciber ="congratulationstoyoucongratulationstoy";
unsigned char str[] =
{
0xBF, 0xD7, 0x2E, 0xDA, 0xEE, 0xA8, 0x1A, 0x10, 0x83, 0x73,
0xAC, 0xF1, 0x06, 0xBE, 0xAD, 0x88, 0x04, 0xD7, 0x12, 0xFE,
0xB5, 0xE2, 0x61, 0xB7, 0x3D, 0x07, 0x4A, 0xE8, 0x96, 0xA2,
0x9D, 0x4D, 0xBC, 0x81, 0x8C, 0xE9, 0x88, 0x78, 0x00
};
unsigned char v31[] =
{
0xBF, 0xD7, 0x2E, 0xDA, 0xEE, 0xA8, 0x1A, 0x10, 0x83, 0x73,
0xAC, 0xF1, 0x06, 0xBE, 0xAD, 0x88, 0x04, 0xD7, 0x12, 0xFE,
0xB5, 0xE2, 0x61, 0xB7, 0x3D, 0x07, 0x4A, 0xE8, 0x96, 0xA2,
0x9D, 0x4D, 0xBC, 0x81, 0x8C, 0xE9, 0x88, 0x78, 0x00
};
unsigned char boom1[] =
{
0xd9, 0xf, 0x18, 0xbd, 0xc7, 0x16, 0x81, 0xbe, 0xf8, 0x4a,
0x65, 0xf2, 0x5d, 0xab, 0x2b, 0x33, 0xd4, 0xa5, 0x67, 0x98,
0x9f, 0x7e, 0x2b, 0x5d, 0xc2, 0xaf, 0x8e, 0x3a, 0x4c, 0xa5,
0x75, 0x25, 0xb4, 0x8d, 0xe3, 0x7b, 0xa3, 0x64, 0x39
};
unsigned char boom2[] =
{
0xde, 0xaa, 0x42, 0xfc, 0x9, 0xe8, 0xb2, 0x6, 0xd, 0x93,
0x61, 0xf4, 0x24, 0x49, 0x15, 0x1, 0xd7, 0xab, 0x4, 0x18,
0xcf, 0xe9, 0xd5, 0x96, 0x33, 0xca, 0xf9, 0x2a, 0x5e, 0xea,
0x2d, 0x3c, 0x94, 0x6f, 0x38, 0x9d, 0x58, 0xea
};
unsigned char ptr[] =
{
0x12, 0x0E, 0x1B, 0x1E, 0x11, 0x05, 0x07, 0x01, 0x10, 0x22,
0x06, 0x17, 0x16, 0x08, 0x19, 0x13, 0x04, 0x0F, 0x02, 0x0D,
0x25, 0x0C, 0x03, 0x15, 0x1C, 0x14, 0x0B, 0x1A, 0x18, 0x09,
0x1D, 0x23, 0x1F, 0x20, 0x24, 0x0A, 0x00, 0x21,0x00
};
for(int i=0;i<39;i++)
{
v31[i]=ciber[i]^str[i];
}
unsigned char transv31[39]={};
memset(transv31,0,sizeof(transv31));
for(int i=0;i<39;i++)
{
v31[i]^=boom2[i];
}
for(int j=0;j<39;j++)
{
transv31[ptr[j]]=v31[j];
}
memcpy(v31,transv31,39);
for(int i=0;i<38;i++)
{
v31[i]^=boom1[i];
}
v31[0]='f';
printf("%s",v31);
return 0;
}
|