第一届OpenHarmony专题赛
本文最后更新于 2025年6月9日 晚上
第一届OpenHarmony专题赛
牢了两天,收获良多。分享一下这次解出的题目。
”任由世界下坠暗夜裹挟,请你聆听一座山的哽咽。在平缓心绪后依旧选择向命运吟唱高歌,在无论是晴是雨的明天里,我还是我,青山依旧巍峨。“
Reverse
easyre
反编译abc看到跟flag有关的逻辑
1 | |
flag由两部分构成,一部分是router.getParams().hint1,另一部分是ldlexvar2.getH2(lexenv_0_1.magic)
第二部分就是标准的base64,在类coder里,但是decodeToString里面有个对字符串的reverse反转操作
1 | |
密文找到是ODg0ZjMxNWYxMDJiMGI4ZGI1NjgwNWYzNGJkYzgxY2ZlYzI,赛博厨子一下得到2cefc18cdb43f50865bd8b0b201f513f488
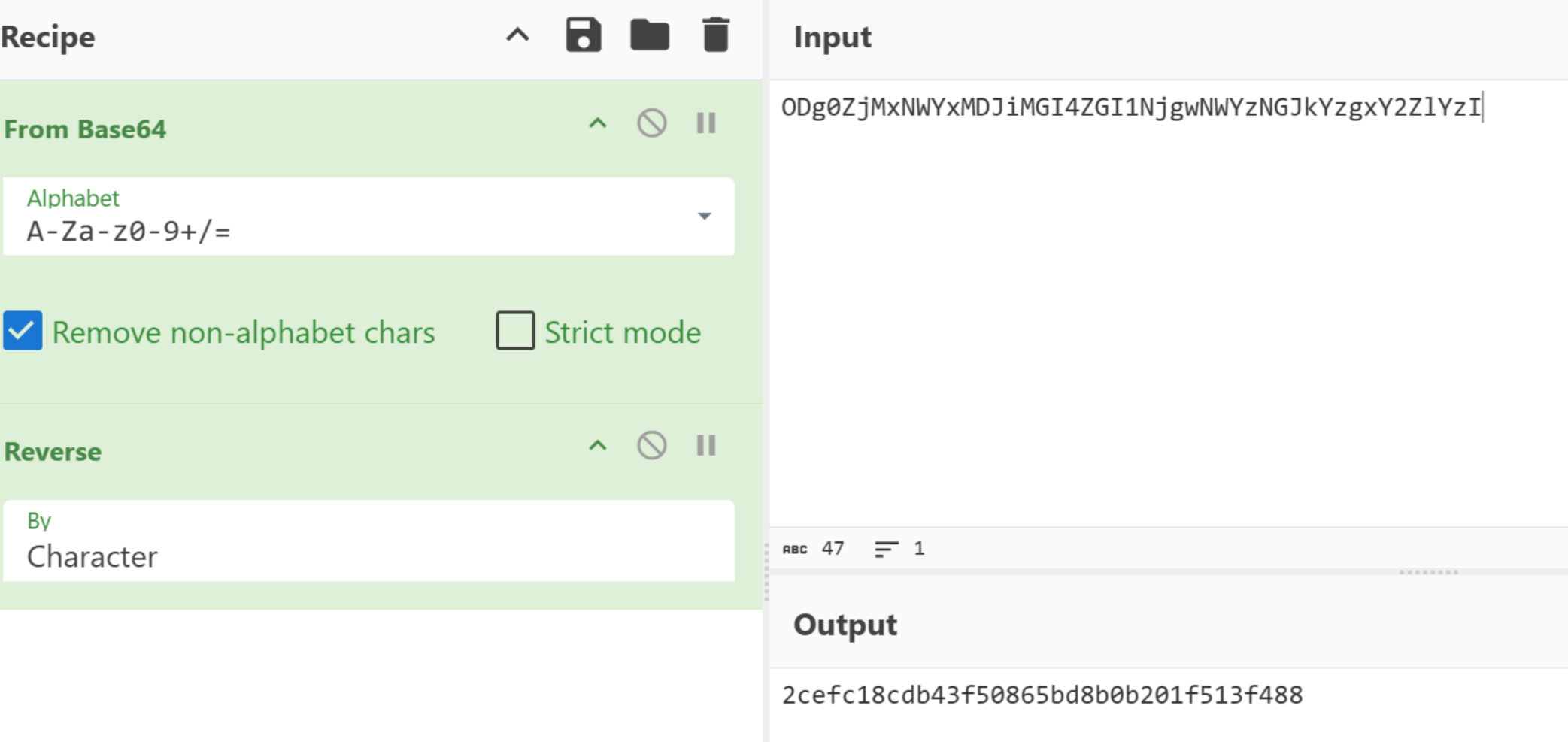
再看对于hint1的处理
1 | |
对字符串先反转再加i再反转再减长度,逆向脚本如下:
1 | |
得到第一部分的结果:princetonuniversity
两部分合起来:flag{princetonuniversity2cefc18cdb43f50865bd8b0b201f513f488}
oh~baby
鸿蒙内核题,qemu启动脚本多了个空格,删了然后正常跑起来,挂载共享文件夹方便拷贝文件
1 | |
给了提示:hcs客户端在/vendor/下
那么去翻/vendor下的目录,在/vendor/bin找到一个chall
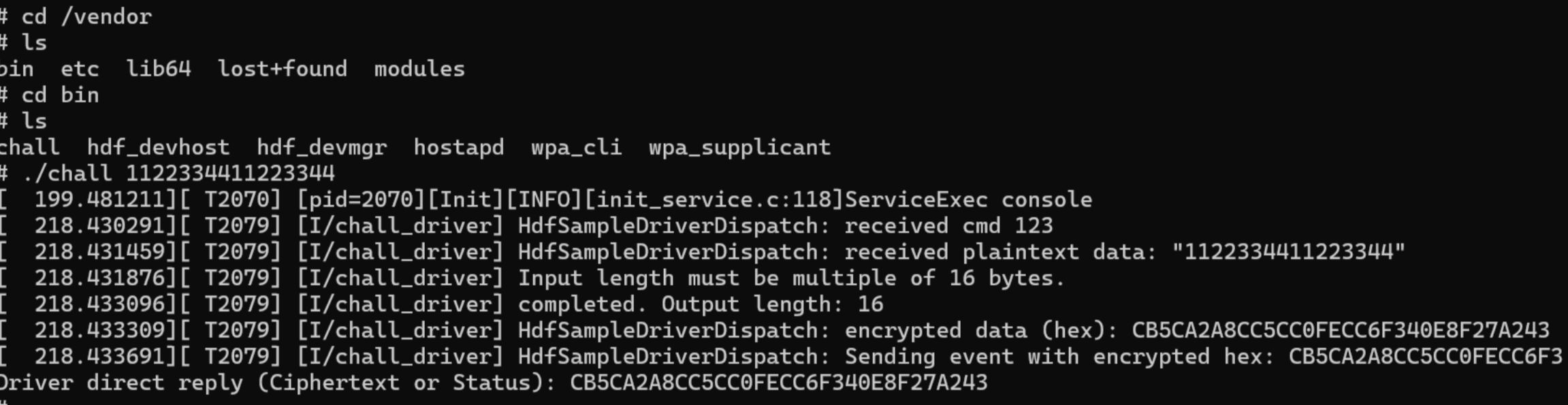
chall是本题的客户端主程序,命令行传参然后会去跟chall_driver驱动交互来进行aes加密,输入长度必须是16的倍数
使用命令cp /vendor/bin/chall /mnt/shared将chall拉下来进行分析
1 | |
v3 = HdfIoServiceBind(“chall_service”);绑定了chall_service这个驱动,但是具体实现逻辑没有体现
尝试利用驱动名find找到了一些信息,比如
/sys/class/hdf/chall_service
/sys/devices/virtual/hdf/chall_service
但均没有驱动的真正逻辑
关注到imgs文件夹里的bzImage,并没有像其他img一样可以解包出系统的文件夹,binwalk -e提取到一个elf 52C4
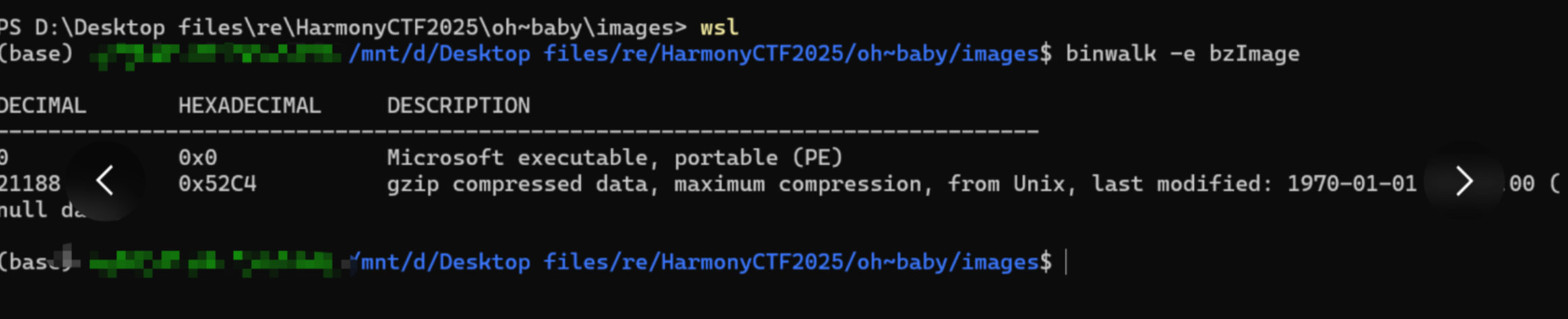
ida分析该elf
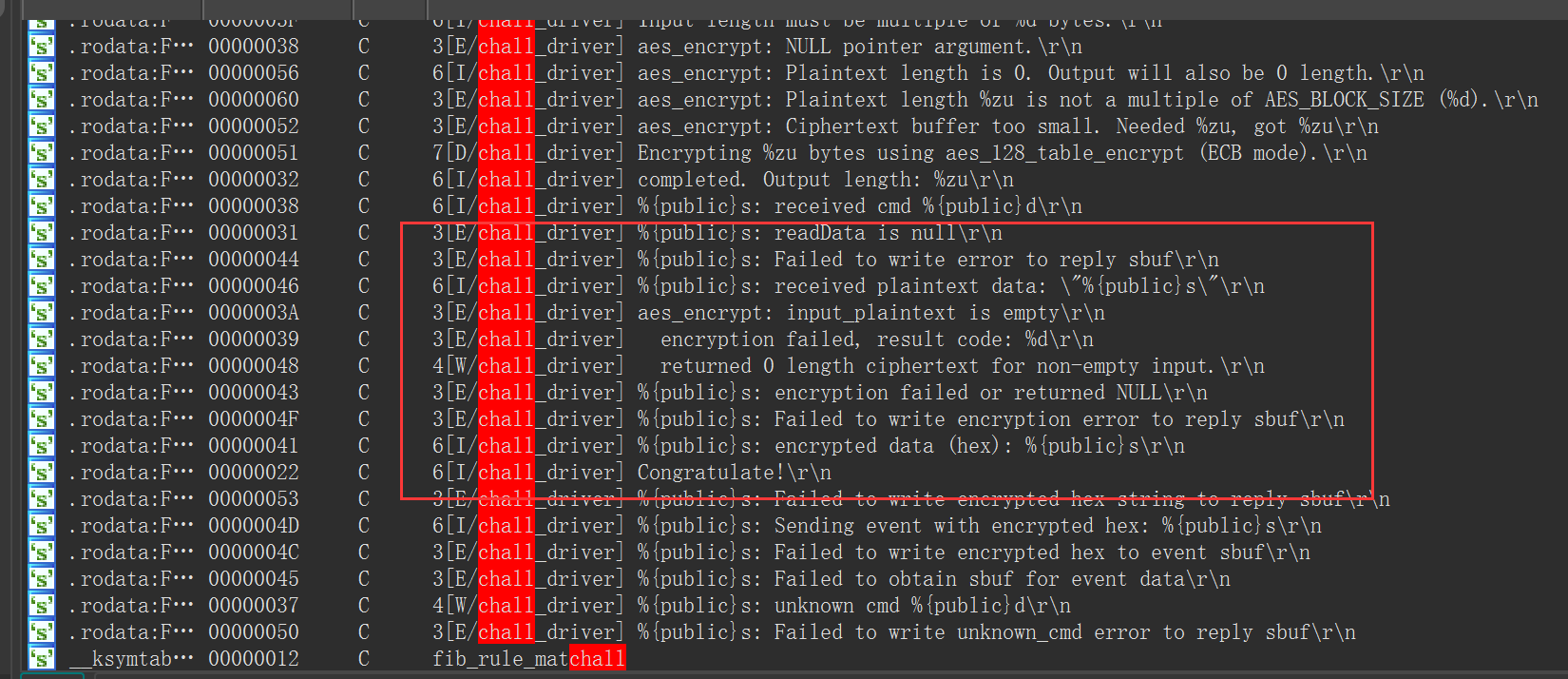
搜驱动名发现有Congratulate一系列的描述,定位到比较函数的位置
1 | |
找到密文是8BE07936ADBB8728D93BB1E0AB715353
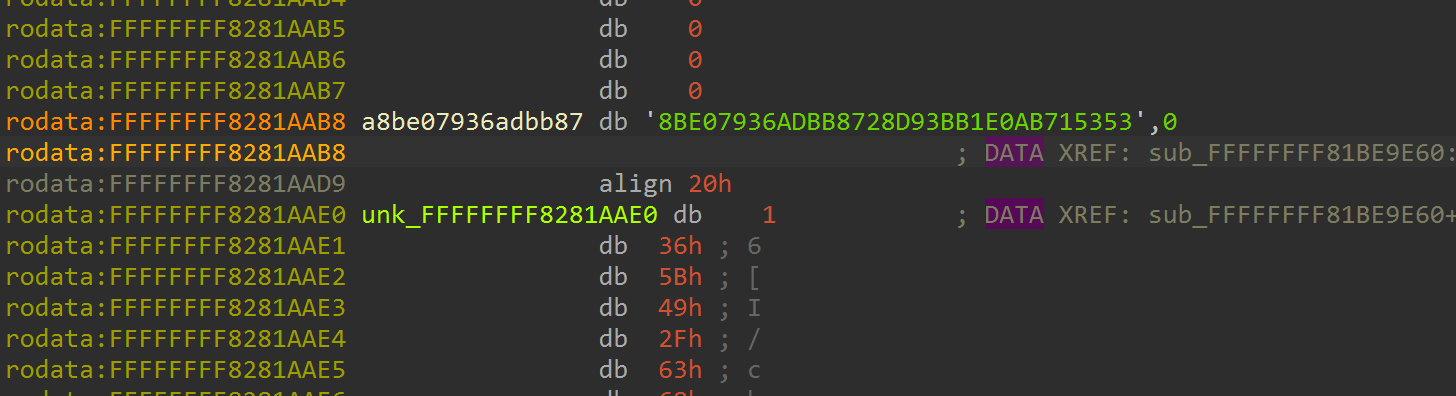
继续分析找到aes的加密逻辑
1 | |
其中
1 | |
其中把密钥v26赋值为0,然后通过字符串确定AES-128-ECB模式,尝试全0密钥解密,得到
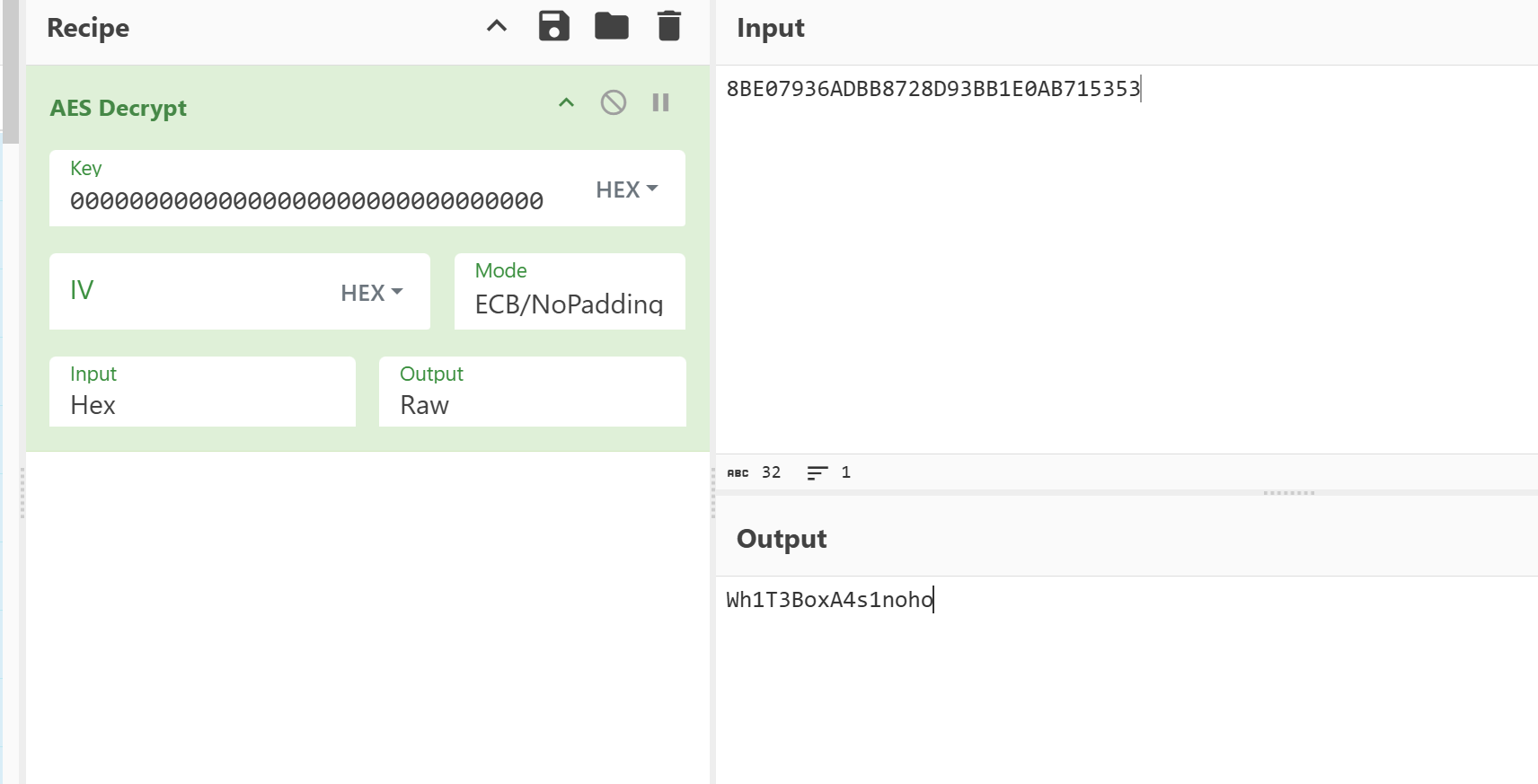 故flag是flag{Wh1T3BoxA4s1noho}
故flag是flag{Wh1T3BoxA4s1noho}
Hardware
easy_designer
第一次在ctf里感受到了专业对口()
题目是电路板,找到使灯亮的输入,开关从(SW01-SW48),如输入01011000,flag为flag{01011000}
使用kicad看整个pcb板子的走线
`键可以高亮走线,看一下从LED引出的线
尝试分析整体的走线,发现所有开关都被调用,那么我们来看pcb板子上的这两种芯片类型
第一种是74LS08 ,这是一款常见的 四路与非门(Quad 2-input AND gate) 芯片,内部有 4 个独立的 2 输入 AND 门。
原理图如下:
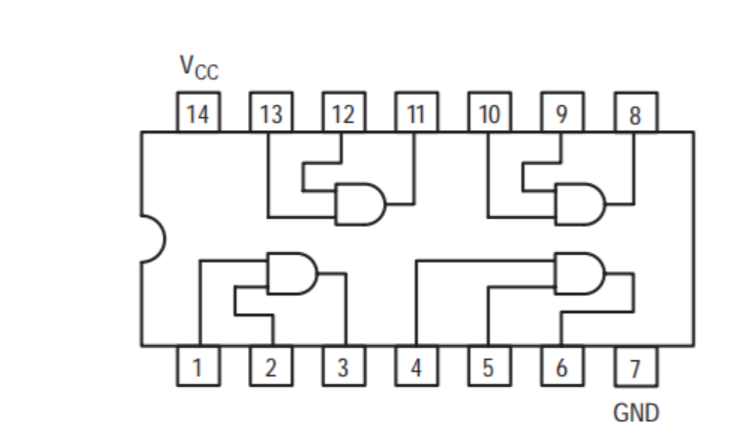
封装:14 脚双列直插(DIP-14)
| 引脚号 | 名称 | 说明 |
|---|---|---|
| 1 | A1 | 第1个门输入 A |
| 2 | B1 | 第1个门输入 B |
| 3 | Y1 | 第1个门输出 Y |
| 4 | A2 | 第2个门输入 A |
| 5 | B2 | 第2个门输入 B |
| 6 | Y2 | 第2个门输出 Y |
| 7 | GND | 地 |
| 8 | Y3 | 第3个门输出 Y |
| 9 | A3 | 第3个门输入 A |
| 10 | B3 | 第3个门输入 B |
| 11 | Y4 | 第4个门输出 Y |
| 12 | A4 | 第4个门输入 A |
| 13 | B4 | 第4个门输入 B |
| 14 | VCC | 电源正(+5V) |
与门的特性是门输入都是1的时候才会输出1
第二种是74AHC04 ,这是一款 六路反相器(Hex Inverter),即它内部包含 6 个独立的 NOT 门(反相器)。每个门有一个输入和一个输出
原理图如下:
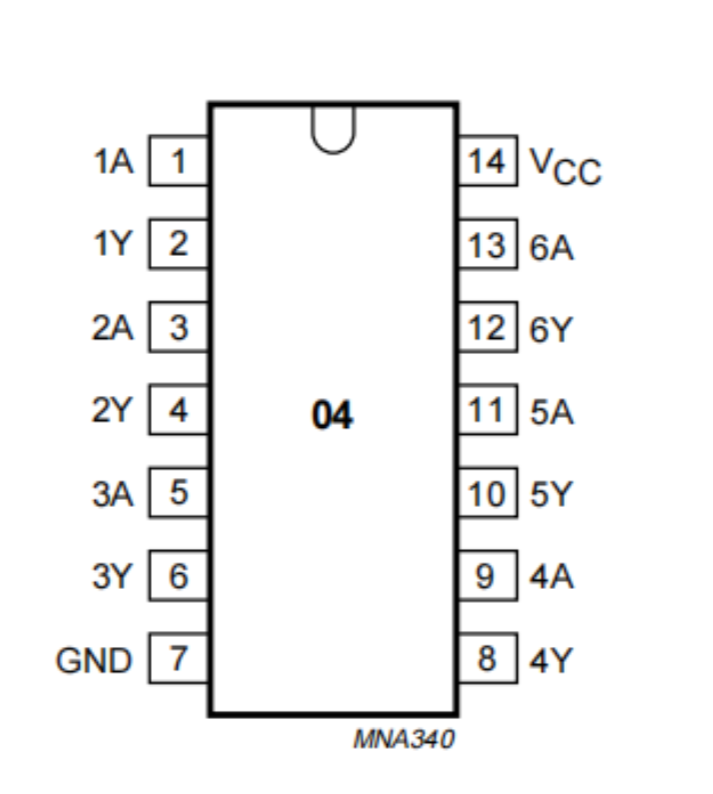
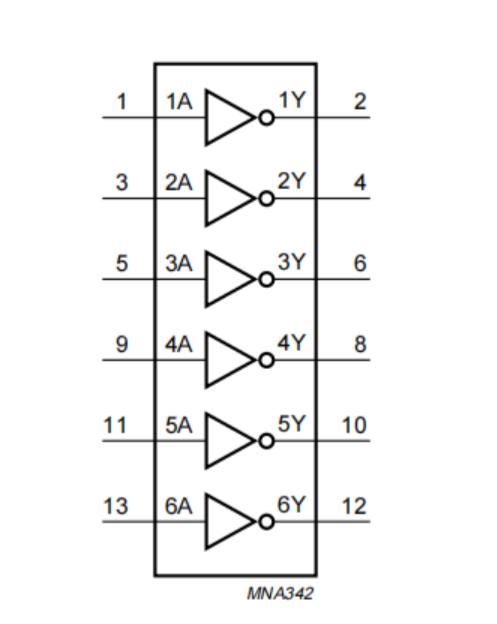
74AHC04 引脚定义(DIP-14 封装)
| 引脚号 | 名称 | 功能说明 |
|---|---|---|
| 1 | A1 | 第1个反相器输入 |
| 2 | Y1 | 第1个反相器输出 |
| 3 | A2 | 第2个反相器输入 |
| 4 | Y2 | 第2个反相器输出 |
| 5 | A3 | 第3个反相器输入 |
| 6 | Y3 | 第3个反相器输出 |
| 7 | GND | 地(0V) |
| 8 | Y4 | 第4个反相器输出 |
| 9 | A4 | 第4个反相器输入 |
| 10 | Y5 | 第5个反相器输出 |
| 11 | A5 | 第5个反相器输入 |
| 12 | Y6 | 第6个反相器输出 |
| 13 | A6 | 第6个反相器输入 |
| 14 | VCC | 电源(+5V) |
非门的特性是输入为0的时候输出为1
那我们可以推测得到位于与门输入的开关对应引脚都需置1,非门输入的开关对应引脚都需置0
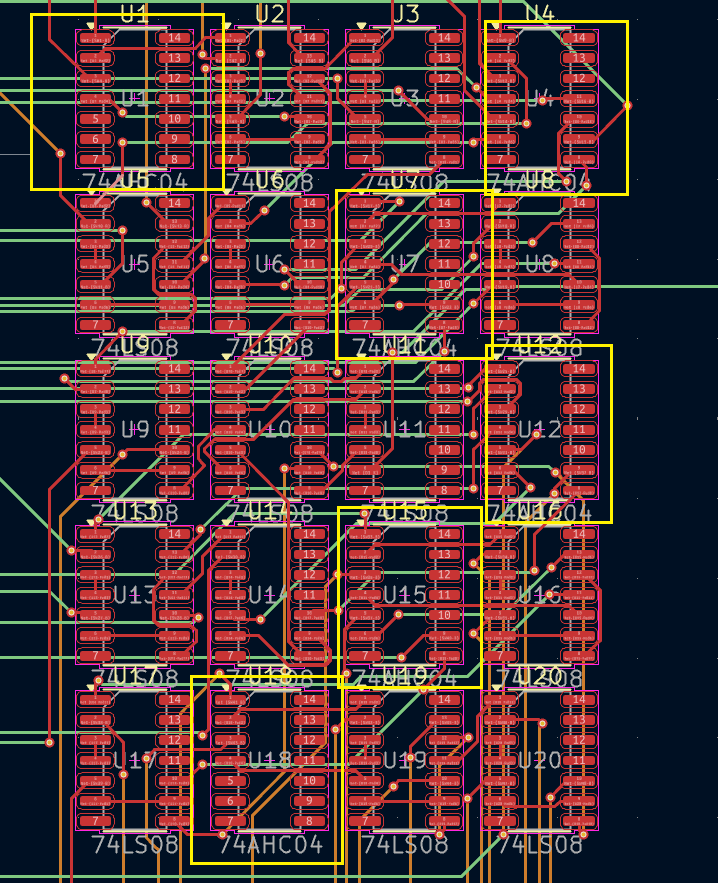
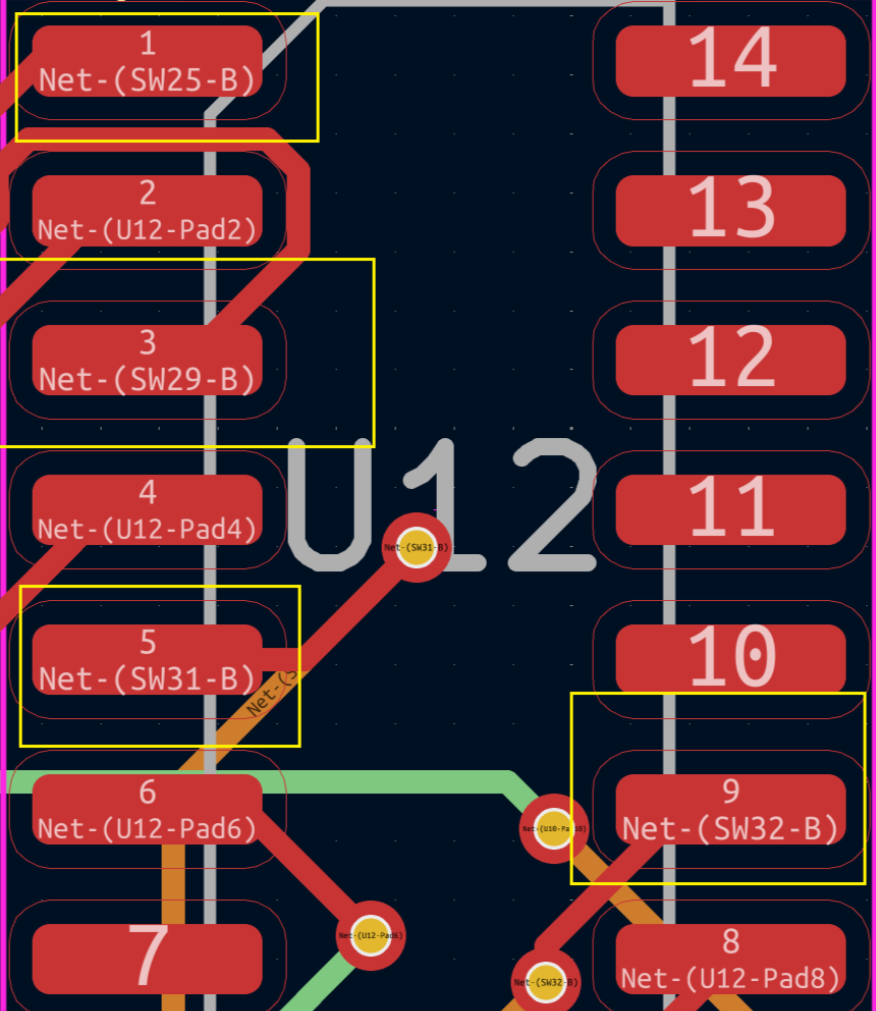
一共有6个74AHC04芯片,位于这些芯片的非门输入端都需置0,如下图的SW25,29,31,32
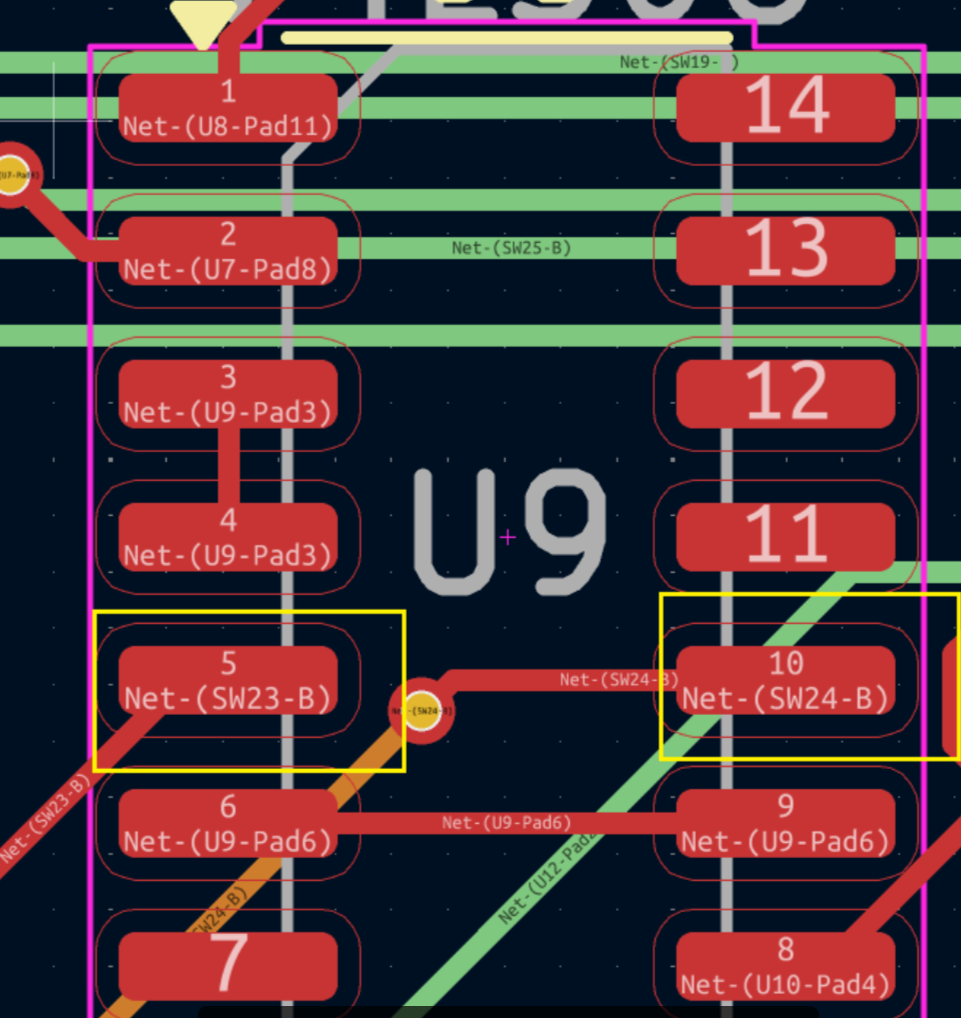
同理 ,74LS08的芯片上面的输入都要置1,如下图的SW23,24
那么统计一下需要置0的开关:
1 4
9
12 14 15
16 17 20
21 22 25
29
31 32 33
36 37 40
41 43
所以整体的序列为011011110110100001100011011101000110011001011111
包上flag{}提交即为答案
写在最后
一直觉得自己没啥进步总在踯躅不前,但是好像每次打比赛都有新的收获和新的肯定出现,仍在路上,仍在努力。
“我想再无风雪滂沱围困生命长河。且看枯木燃成烈火,用青山诠释我,生生不息的磅礴。”